How To Determine If Your Computer Is Being Assigned The External IP Address
For Windows 2000, XP, and 2003
Access eLite's
HTTP Tunneling,
ipconfig,
proxy pattern,
proxy statistics,
proxy voting,
proxy war,
tunnel
How To Trace An Email
How To Trace An Email
What is an email header?
Each email you receive comes with headers. The headers contain information about the routing of the email and the originating IP of the email. Not all emails you receive can be traced back to the originating point and depending on how you send emails determines whether or not they can trace the email back to you. The headers don't contain any personal information. At most, you can get the originating IP and the computer name that sent the email.
Access eLite's
Email,
GMail,
header,
Hotmail,
How To Trace,
ip,
Outlook,
Windows Live Mail,
X-Originating IP,
Yahoo
How To Trace An Email
How To Trace An Email
What is an email header?
Each email you receive comes with headers. The headers contain information about the routing of the email and the originating IP of the email. Not all emails you receive can be traced back to the originating point and depending on how you send emails determines whether or not they can trace the email back to you. The headers don't contain any personal information.
Access eLite's
Email,
External IP Address,
trace,
X-Originating IP
Dos / Windows Ip Commands
Dos / Windows Ip Commands
Display Connection Configuration: ipconfig /all
Display DNS Cache Info: ipconfig /displaydns
Clear DNS Cache: ipconfig /flushdns
Release All IP Address Connections: ipconfig /release
Renew All IP Address Connections:
Display DNS Cache Info: ipconfig /displaydns
Clear DNS Cache: ipconfig /flushdns
Release All IP Address Connections: ipconfig /release
Renew All IP Address Connections:
Access eLite's
An IP address,
Change IP Address,
ip,
IP address,
ip commands
How To Change Your IP Address
How To Change Your IP Address
There are MANY methods to change your IP address. Some methods will work for you but may not work for someone else and vice versa.
If your IP is static, then you CAN’T change your IP address without contacting your ISP.
If you have a long lease time (explained in this article) on your IP then you won’t be able to change your IP without cloning your MAC address, which I’ll explain later in this article.
It definitely helps if you know how the IP is being assigned to you.
Access eLite's
Change IP Address,
ip,
IP address,
mac
Prevent changes in setting Password
Prevent changes in setting Password
If you enable this setting, then other people can not change settings in the Control Panel - Password.
In other words, other people can not change the password (if your computer using the Windows password).
If you enable this setting, then other people can not change settings in the Control Panel - Password.
In other words, other people can not change the password (if your computer using the Windows password).
Access eLite's
control panel,
CURRENT,
Password,
regedit
Open Port Check Tool
Open Port Check Tool
Most residential ISP's block ports to combat viruses and spam. The most commonly blocked ports are port 80 and port 25.
An IP address
An IP address
An IP address can also be thought of as the equivalent of a street address or a phone number for a computer or other network device on the Internet. Just as each street address and phone number uniquely identifies a building or telephone, an IP address can uniquely identify a specific computer or other network device on a network.
Access eLite's
An IP address,
External IP Address,
ip,
IP address,
vpn
Static And Dynamic Ip address
Static And Dynamic Ip address
A Static IP address is where a computer uses the same address every time, as opposed to situations where the user IP address changes frequently, when a user logs on to a network by dialup or on shared residential cable. Static addressing is essential in some infrastructure situations, such as finding the Domain Name Service directory host that will translate names to numbers.
Access eLite's
An IP address,
Change IP Address,
External IP Address,
ip,
IP address,
Static And Dynamic Ip
External IP Address
What is an External IP Address
An external IP address is the unique identifier assigned to you by your Internet Service Provider (ISP). There are to types of external IP address, static and dynamic. Static is fixed and therefore never changes. Dynamic changes every time you connect to the internet.
Access eLite's
An IP address,
Change IP Address,
External IP Address,
ip,
IP address,
Static And Dynamic Ip
Impact of global warming
Impact of global warming
1. Climate Not Start Stable
The scientists predict that during global warming, the North region of the Earth North (Northern Hemisphere) akan heat more than other areas on the Earth. As a result, the mountains will melt ice and land will decline. Akan less ice that float on the waters of the North. Areas that previously experienced light snow, it may not feeling again. In the mountains in subtropical areas, the snow-covered will be less and will melt more quickly. The planting season will be longer in some areas. Temperatures during the winter nights and days will tend to increase.
1. Climate Not Start Stable
The scientists predict that during global warming, the North region of the Earth North (Northern Hemisphere) akan heat more than other areas on the Earth. As a result, the mountains will melt ice and land will decline. Akan less ice that float on the waters of the North. Areas that previously experienced light snow, it may not feeling again. In the mountains in subtropical areas, the snow-covered will be less and will melt more quickly. The planting season will be longer in some areas. Temperatures during the winter nights and days will tend to increase.
Access eLite's
climate,
global warming,
impact
The cause of global warming
The cause of global warming
1.Effect greenhouse
Any source of energy found in the Earth comes from the sun. Most of the energy in the form of short wave radiation, including visible light. When this energy surface of the Earth arrived, he changed from light into heat that warm the Earth. Surface of the Earth, will absorb some heat and toss the rest back. Part of this substantial heat infra red radiation wave length to outer space. However, some heat remains trapped in the earth's atmosphere due
1.Effect greenhouse
Any source of energy found in the Earth comes from the sun. Most of the energy in the form of short wave radiation, including visible light. When this energy surface of the Earth arrived, he changed from light into heat that warm the Earth. Surface of the Earth, will absorb some heat and toss the rest back. Part of this substantial heat infra red radiation wave length to outer space. However, some heat remains trapped in the earth's atmosphere due
Access eLite's
earth,
effect,
global warming
Drugs Informations
Drugs
Is the abbreviation of drugs and drug addict drugs / hazardous materials. In addition to "drugs", another term introduced especially by the Ministry of Health of the Republic of Indonesia is Napza which is the abbreviation of 'drug addict, and psychotropic substance Adiktif'.
Is the abbreviation of drugs and drug addict drugs / hazardous materials. In addition to "drugs", another term introduced especially by the Ministry of Health of the Republic of Indonesia is Napza which is the abbreviation of 'drug addict, and psychotropic substance Adiktif'.
Access eLite's
addict,
Adiktif,
Controversy,
Drug Rehab,
Drug Rehab Program,
Drugs,
Drugs Informations,
Halusinogen,
Heroin,
Stimulation
IP (Internet Protocol) & Hostname
IP (Internet Protocol) & Hostname
IP (Internet Protocol) address is used to identify your computer on a network. It's a way computers recognize each other. Your IP address can change. Sometimes often. It depends on your Internet Service Provider and the type of service you have with them.
Each machine connected to the Internet has an address known as an Internet Protocol address (IP address). The IP address takes the form of four numbers separated by dots, for example: 123.45.67.890.
Hostname refers to the unique name that identifies a computer on a network.
On the Internet, the host name is in the form "computer.123.net"; if there is only one Internet site the host name is the same as the domain name. One computer can have more than one host name if it hosts more than one Internet site, however (for example, "desk.123.net" and "room.123.net"); in that case "desk" and "room" are host names and "123.net" is the domain name.
IP (Internet Protocol) address is used to identify your computer on a network. It's a way computers recognize each other. Your IP address can change. Sometimes often. It depends on your Internet Service Provider and the type of service you have with them.
Each machine connected to the Internet has an address known as an Internet Protocol address (IP address). The IP address takes the form of four numbers separated by dots, for example: 123.45.67.890.
Hostname refers to the unique name that identifies a computer on a network.
On the Internet, the host name is in the form "computer.123.net"; if there is only one Internet site the host name is the same as the domain name. One computer can have more than one host name if it hosts more than one Internet site, however (for example, "desk.123.net" and "room.123.net"); in that case "desk" and "room" are host names and "123.net" is the domain name.
Access eLite's
host names,
hostname,
internet protocol,
ip
What is VoIP?
What is VoIP?
VoIP (Voice over Internet Protocol) is simply the transmission of voice traffic over IP-based networks.
The Internet Protocol (IP) was originally designed for data networking. The success of IP in becoming a world standard for data networking has led to its adaption to voice networking.
The Economics of VoIP
VoIP has become popular largely because of the cost advantages to consumers over traditional telepone networks. Most Americans pay a flat monthly fee for local telephone calls and a per-minute charge for long-distance calls.
VoIP calls can be placed across the Internet. Most Internet connections are charged using a flat monthly fee structure.
Using the Internet connection for both data traffic and voice calls can allow consumers to get rid of one monthly payment. In addition, VoIP plans do not charge a per-minute fee for long distance.
For International calling, the monetary savings to the consumer from switching to VoIP technology can be enormous.
VoIP Telephones
There are three methods of connecting to a VoIP network:
- Using a VoIP telephone
- Using a "normal" telephone with a VoIP adapter
- Using a computer with speakers and a microphone
Types of VoIP Calls
VoIP telephone calls can be placed either to other VoIP devices, or to normal telephones on the PSTN (Public Switched Telephone Network).
Calls from a VoIP device to a PSTN device are commonly called "PC-to-Phone" calls, even though the VoIP device may not be a PC.
Calls from a VoIP device to another VoIP device are commonly called "PC-to-PC" calls, even though neither device may be a PC.
Recent advances in Voice over IP (VoIP) technology have made it the solution of choice for voice service because of its low cost and increased reliability. VoIP Crash Course offers practical technology coverage, while discussing the business, strategic and competitive implications of VoIP deployment in corporations. The book also covers the challenges faced by service providers as they evolve to an IP infrastructure while continuing to operate the PSTN.
Access eLite's
PSTN,
telephone,
Types of VoIP Calls,
voip,
VoIP network,
VoIP telephone
What are Search Engines?
What are Search Engines?
Search engines are specialized websites designed to help people find the information they need quickly and easily on the internet. While each search engine (e.g. Google, Yahoo!Search, etc.) have different approaches to data gathering, they all perform three core functions:
- Searching or surfing the internet based on important words;
- Keeping an index of what they find and where they found them; and
- Allow users to look for words or combinations of words on their site.
Access eLite's
etc,
Google,
Search Engines,
Yahoo
How to block pop ups in Internet Explorer
How to block pop ups in Internet Explorer
If there is one thing which is hated by every web surfer, then it has to be these pop ups which comes from no where on your face.
What are pop-ups ?
There are two categories of pop-ups; general web browser pop-ups and pop-ups created by spyware and adware. These two categories can be differentiated by a few distinct characteristics.
Imagine a case where you are browsing an online store and suddenly a pop-up window is prompted as an advertisement. This pop-up definitely interferes with your ability to see the page content and distracts you from what you were doing. Therefore, blocking the pop-ups will ease your online experience.
How to block pop ups ?
There are two ways of blocking pop-ups; manually and using a web browser toolbar.
Manually
Note: You need to have Windows XP Service Pack 2 installed in order to follow the below steps as ‘Pop-up Blocker’ is installed with SP2.
Internet Explorer 6 / 7
1. Open Internet Explorer.
2. Go to ‘Tools’ menu and select ‘Pop-up Blocker’.
3. Click ‘Turn on Pop-up Blocker’.
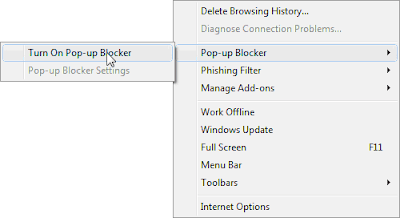
In some websites, pop-ups are displayed when you click a button or a link. The above procedure does not block this type of pop-ups and that needs to be set by following below steps;
1. Open Internet Explorer.
2. Go to ‘Tools’ menu and select ‘Pop-up Blocker’.
3. Now click ‘Pop-up Blocker Settings’.
4. Select ‘High’ in the ‘Notification and Filter Level’ placed at the bottom of the dialog box.
Blocking pop ups by Using a Toolbar
Since pop-ups have become a critical issue for positive Internet user experience, many Internet companies have included pop-up blocking facility in the respective web browser toolbars.
Google Toolbar
Google toolbar blocks pop-ups once it is downloaded and installed in your web browser. This toolbar is offered for Internet Explorer and Mozilla Firefox by Google. Compared to its competitors, Google toolbar is considered efficient and accurate in blocking pop-ups.
Yahoo! Toolbar
Yahoo! toolbar is one of the first browser toolbars that introduced pop-up blocking. It still continues to offer this feature and should be offering this pop up block feature for Internet explorer.
Access eLite's
block pop ups,
google toolbar,
mozilla,
op-up blocker,
pop-up blocker settings,
toolbar,
yahoo toolbar
Register with Blogger or Create an Account
Register with Blogger or Create an Account
Before start blogging you must have a account and if you want to start with Blogger, then you have to register your self on it, or if you are google you can use your google account id and password. You must know that google provide many services and you can use your one google account with all services Like
1. Google
2. Blogger
3. Adsense
4. Docs
5. Orkut
6. Youtube
and many more>>>
1. Google
2. Blogger
3. Adsense
4. Docs
5. Orkut
6. Youtube
and many more>>>
Access eLite's
Create an Account
Credit card
Credit card
A credit card is part of a system of payments named after the small plastic card issued to users of the system. It is a card entitling its holder to buy goods and services based on the holder's promise to pay for these goods and services. The issuer of the card grants a line of credit to the consumer (or the user) from which the user can borrow money for payment to a mercant or as a cash advence to the user.
A credit card is different from a charge card, where a charge card requires the balance to be paid in full each month. In contrast, credit cards allow the consumers to 'revolve' their balance, at the cost of having interest charged. Most credit cards are issued by local banks or credit unions, and are the shape and size specified by the ISO/IEC 7810 standard as ID-1.
Access eLite's
banks,
Credit card,
credit unions,
payments
Register a URL
Register a URL
How Do You Register a URL?
Registering a URL can be a very straightforward process, provided that your business can be flexible in terms of its cyberspace designations. There are literally hundreds of online registration sites which can walk you through the process -- some charge more than others for premium services such as helping you create a prefab web page or providing suggestions for alternative names for your site.
Registration works much like real estate renting and buying. You can register a URL for a web site for a discrete period of time. For instance, if you are setting up a wedding web site, you can rent an HTTP URL from the period of your engagement to a few months after your wedding. If you run a business which may need to grow and expand (and hence shed a few URL names in the process), this “renting” of URL space may make the most sense.
Alternatively, you can buy addresses outright and even sell sub-domains within your URL to other companies. Web site business mavens recommend that entrepreneurs stick to .com URLs when possible. If you have a brand or trademark that must be the primary URL designation, consider alternative first-level domains like .net or .tv. With that said, be aware that all non-.com web site run the risk of accidentally driving traffic to their .com dopplegangers.
Remember that just because you register your URL doesn’t mean you’re necessarily registered with the search engines. You may have to go to each one of the major engines to identify your web site as an e-business. Investigate any companies which claim to be able to register your URL for you.
While many of these services are indeed legitimate and useful, there are troublemakers and scam artists out there. You may refer any specious web site URL registration services to your local Better Business Bureau. Consumer protection agencies (especially nonprofit ones) can also clue you into safe URL registration facilities.
How Do You Register a URL?
The concept of a uniform resource locator (URL) derives from Tim Berners-Lee’s early work on hypertext during the late 1980s and early 1990s. Fortunately, you don’t have to learn the history of HTTP and hypertext to develop a portal for your web site in cyberspace.
Registering a URL can be a very straightforward process, provided that your business can be flexible in terms of its cyberspace designations. There are literally hundreds of online registration sites which can walk you through the process -- some charge more than others for premium services such as helping you create a prefab web page or providing suggestions for alternative names for your site.
Registration works much like real estate renting and buying. You can register a URL for a web site for a discrete period of time. For instance, if you are setting up a wedding web site, you can rent an HTTP URL from the period of your engagement to a few months after your wedding. If you run a business which may need to grow and expand (and hence shed a few URL names in the process), this “renting” of URL space may make the most sense.
Alternatively, you can buy addresses outright and even sell sub-domains within your URL to other companies. Web site business mavens recommend that entrepreneurs stick to .com URLs when possible. If you have a brand or trademark that must be the primary URL designation, consider alternative first-level domains like .net or .tv. With that said, be aware that all non-.com web site run the risk of accidentally driving traffic to their .com dopplegangers.
Hence, if you register a .int web site in your name, you may
assist the rival that took your .com name in the first place.
Remember that just because you register your URL doesn’t mean you’re necessarily registered with the search engines. You may have to go to each one of the major engines to identify your web site as an e-business. Investigate any companies which claim to be able to register your URL for you.
While many of these services are indeed legitimate and useful, there are troublemakers and scam artists out there. You may refer any specious web site URL registration services to your local Better Business Bureau. Consumer protection agencies (especially nonprofit ones) can also clue you into safe URL registration facilities.
- register a website -
Access eLite's
Register a URL,
register a website,
registration,
uniform resource locator,
URL
Car Insurance
Car Insurance
Online Car Insurance Quotes are a great demonstration of how the internet is changing the way we all do business. Gone are the days of visiting your local insurance agent and accepting whatever price you are quoted on auto insurance from the only company he maintains an agency relationship with. Today, competitive car insurance comparisons online allow consumers to quickly compare rates among various car insurance carriers with no obligation. You submit some basic information about your automobiles, driving history etc., and generally quotes from competing companies will be displayed instantly. If you wish to follow-up on a particular insurance rate quote, simply click on the link for that quote to make further inquiry. Car insurance has essentially become a commodity with states heavily regulating coverage options. Thus, there is no reason not to explore the savings you can get by comparing auto insurance quotes online.
Access eLite's
car Insurance,
insurance
How to find my ISP
How to find my ISP
In case you want to know full name of your ISP there are many ways to find it. First of all you need to find out the Global IP address of your system or the Default Gateway of your ISP.
The IP address you get from commands like “ipconfig/all” or “ipconfig” is your local network IP and which is different from the global IP address. The global IP address is assigned to your system by your Internet Service Provider. Now, you can get your global IP address easily from websites below without doing anything, just open any of these sites…
Now, you need to find any geo location service which can tell which ISP has assigned that IP for you. IP2Location is such a service from where you can easily get the ISP name and the nearest node of your Internet Service Provider like the screenshot below. IP2Location allow you to find 200 IP Locations for free per day.
Access eLite's
check,
gateway,
ip,
ip2location,
isp
Top 7 Ways to Secure Windows XP
Top 7 Ways to Secure Windows XP
1. Turn on Automatic Updates in Windows XP
Automatic Updates is a Windows XP utility that allows your computer to download security updates from Microsoft automatically. Turning on Automatic Updates helps to secure your computer since you'll always have the latest critical security updates.
2. Turn on the Free Firewall in Windows XP
If you have Service Pack 2 installed, you have a free firewall that you can use to protect your computer from attacks. However, you must turn the free firewall on.
While the free firewall in Windows XP provides some protection, learn why Windows Firewall may not be enough.
3. Use Internet Explorer Wisely
Internet Explorer 6 provides four zones for which you can establish seperate security settings. By using the four zones, you'll reduce your chances of being the victim of an attack when you inadvertently visit a malicious Web site.
4. Use Anti-Virus Software
Viruses can reak havoc on your computer. Protect yourself by using antivirus software. There are many antivirus programs to choose from, but the About Guide to Antivirus Software provides a list of the Top 7 Antivirus Programs for Windows.
5. Use Spyware and Adware Software
Spyware is software that allows companies to monitor what websites you visit or even access your computer. Adware is software that displays advertisements. Protect your computer by using spyware and adware software.
6. Be Careful What You Click On
Often, attackers must entice you to open an email attachment or visit their Web site in order to attack your computer. If you open the attachment or visit their site, malicious code is executed on your computer. To protect your computer, be careful what you click on.
7. Use Limited Accounts to Better Secure Your Windows XP Computer
It's harder for someone to attack your computer through the Internet if you're using a limited account. Learn why it's best to use limited accounts for daily use and how to create a limited account.
1. Turn on Automatic Updates in Windows XP
Automatic Updates is a Windows XP utility that allows your computer to download security updates from Microsoft automatically. Turning on Automatic Updates helps to secure your computer since you'll always have the latest critical security updates.
2. Turn on the Free Firewall in Windows XP
If you have Service Pack 2 installed, you have a free firewall that you can use to protect your computer from attacks. However, you must turn the free firewall on.
While the free firewall in Windows XP provides some protection, learn why Windows Firewall may not be enough.
3. Use Internet Explorer Wisely
Internet Explorer 6 provides four zones for which you can establish seperate security settings. By using the four zones, you'll reduce your chances of being the victim of an attack when you inadvertently visit a malicious Web site.
4. Use Anti-Virus Software
Viruses can reak havoc on your computer. Protect yourself by using antivirus software. There are many antivirus programs to choose from, but the About Guide to Antivirus Software provides a list of the Top 7 Antivirus Programs for Windows.
5. Use Spyware and Adware Software
Spyware is software that allows companies to monitor what websites you visit or even access your computer. Adware is software that displays advertisements. Protect your computer by using spyware and adware software.
6. Be Careful What You Click On
Often, attackers must entice you to open an email attachment or visit their Web site in order to attack your computer. If you open the attachment or visit their site, malicious code is executed on your computer. To protect your computer, be careful what you click on.
7. Use Limited Accounts to Better Secure Your Windows XP Computer
It's harder for someone to attack your computer through the Internet if you're using a limited account. Learn why it's best to use limited accounts for daily use and how to create a limited account.
Mac Data Recovery
Mac Data Recovery
Disk Utility is a tool that is created for performing disk-related operations and it comes equipped with Mac OS X. It is used for mounting hard drive, verifying disk integrity, disk formatting and partitioning, disabling or enabling journaling and creation of disk images. Disk Utility is undoubtedly a useful utility, but in some version of Mac OS X, it may not function properly. Particularly in Mac OS X 10.5 Leopard, Disk Utility may show unexpected behavior when you try to change, delete or format a hard drive volume. This issue may lead to Mac Data Recovery solutions.
When you attempt to modify, remove or format a Mac OS X 10.5 Leopard volume, you might come across the below given error message:
“File system formatter failed”
This issue generally occurs when your try to change the file system of a particular Mac OS X volume. The problem could be due to:
> This problem could be due to incompatibility of Mac OS X Leopard Disk Utility with the disk partitioning scheme, which is used by Leopard.
> If the Partition Table is corrupted, the Disk Utility might fail to change or format the Mac OS X volumes.
This whole behavior of Mac OS X makes your hard drive volumes and critical data inaccessible and results into serious data loss situations. This situation requires Mac Recovery to be fixed.
Resolution
In order to fix this issue, Mac OS X disk requires to be repartitioned using the Disk Utility. For repartitioning a hard drive using Disk Utility, go through the given steps:
> Open Disk Utility, select the disk which you want to partition and click Partition tab.
> From drop-down list, select number of partitions needed.
> Using ‘Options’ button, select partition type.
> Set required partition size and click ‘Partition’.
In order to fix this issue, Mac OS X disk requires to be repartitioned using the Disk Utility. For repartitioning a hard drive using Disk Utility, go through the given steps:
> Open Disk Utility, select the disk which you want to partition and click Partition tab.
> From drop-down list, select number of partitions needed.
> Using ‘Options’ button, select partition type.
> Set required partition size and click ‘Partition’.
Although, this method is able to resolve the issue, but repartitioning also deletes all the hard drive volumes and data stored on them. In such cases, you should carry out Data Recovery Mac to get all your critical data back.
Recovery is best possible with the help of third party Mac Recovery software. These software are capable of systematically scanning entire Mac OS X hard drive and recover all of the data from it. These software are fairly easy to use and perform safe recovery.
Stellar Phoenix Macintosh Data Recovery is the most advanced tool to recover lost, missing or inaccessible Mac OS X partitions and data. This software recovers data from all HFS, HFS+, HFSX, HFS Wrapper and FAT file system volumes. It is compatible with Mac OS X 10.5, 10.4 and 10.3.9.
Recovery is best possible with the help of third party Mac Recovery software. These software are capable of systematically scanning entire Mac OS X hard drive and recover all of the data from it. These software are fairly easy to use and perform safe recovery.
Stellar Phoenix Macintosh Data Recovery is the most advanced tool to recover lost, missing or inaccessible Mac OS X partitions and data. This software recovers data from all HFS, HFS+, HFSX, HFS Wrapper and FAT file system volumes. It is compatible with Mac OS X 10.5, 10.4 and 10.3.9.
Access eLite's
data recovery,
drive,
mac data recovery,
partition,
reconery,
system
Car Accident
Car Accident
If you or a loved one has been in a minor or fatal a car accident, you need an experienced car accident lawyer to help you get the financial compensation you deserve. Your car accident lawyer at Weitz & Luxenberg works on contingency. That means you get a FREE Car Accident Lawyer unless we win your car accident lawsuit. Your car accident lawyer only gets paid if you get paid.
Car accidents fall into several major categories:
> Rear-end collisions
> Side collisions
> Rollovers
> Head-on collisions
> Single-car accidents
> Pile-ups
Collisions can be dangerous. If you experience a collision with another driver, bicyclist, or pedestrian tell us about it. We can explain your legal options.> Side collisions
> Rollovers
> Head-on collisions
> Single-car accidents
> Pile-ups
The weakest part of a car is the side. If you sufer a side-door collision this could cause more damage than being hit from the front or the back. The party most likely to be injured is the occupant of the car that weighs less.
Access eLite's
Accident,
Car Accident,
car accident lawyer,
lawyer
Drug Rehab
Drug Rehab Program
The question of “why should I go to a drug rehab program” is one that causes more discussion and doubt, anger and distrust, arguments and apathy than any other question associated with addiction. So why all the fuss? When a person is locked in the grasp of addiction, even the torture of ripping everything that matters away from them often doesn’t outweigh the tremendous craving to use more drugs. A family member may look at the person and think “ how could you not see how desperate your situation is” or “you must not want to get your life back so you must enjoy this struggle and pain”.
The truth is that no addict wants to be an addict. No one every woke up one morning and decided to rip apart their family, doom themselves to unemployed, penniless reliance on anyone who will support them and ultimate death or imprisonment for the drug or alcohol that controls them. Still, millions seem like they choose exactly that every day.
Families try to help and the subject of drug rehab or alcohol addiction treatment is brought up only to produce resistance, argument, denial of the problem and resentment among everyone trying to help.
There are very clear cut reasons why this often occurs and there are really effective ways to slice through all this agonizing debate and struggle and get the person to realize they need help. Our counselors are trained to help you achieve just that. Call us today before addiction takes another life by confusion, indecisive apathy and a continued problem. No one deserves to die a drug and alcohol addict. Start the recovery process today.
The question of “why should I go to a drug rehab program” is one that causes more discussion and doubt, anger and distrust, arguments and apathy than any other question associated with addiction. So why all the fuss? When a person is locked in the grasp of addiction, even the torture of ripping everything that matters away from them often doesn’t outweigh the tremendous craving to use more drugs. A family member may look at the person and think “ how could you not see how desperate your situation is” or “you must not want to get your life back so you must enjoy this struggle and pain”.
The truth is that no addict wants to be an addict. No one every woke up one morning and decided to rip apart their family, doom themselves to unemployed, penniless reliance on anyone who will support them and ultimate death or imprisonment for the drug or alcohol that controls them. Still, millions seem like they choose exactly that every day.
Families try to help and the subject of drug rehab or alcohol addiction treatment is brought up only to produce resistance, argument, denial of the problem and resentment among everyone trying to help.
There are very clear cut reasons why this often occurs and there are really effective ways to slice through all this agonizing debate and struggle and get the person to realize they need help. Our counselors are trained to help you achieve just that. Call us today before addiction takes another life by confusion, indecisive apathy and a continued problem. No one deserves to die a drug and alcohol addict. Start the recovery process today.
Access eLite's
addict,
Drug Rehab,
Drug Rehab Program
MBA Degree Online
MBA Degree Online
Online MBA Degree Programs
The decision to pursue an Online MBA could not be made at a better time. Employers today are demanding more education from their employees than ever before. An accredited online MBA degree will carry significant value in any organization's hiring and career advancement decisions. Plus, there is a direct correlation between higher salaries and earning and MBA.
In difficult economic times, going back to school to build new skills -- and make yourself more attractive to future employers -- becomes extremely popular, even for people with full-time jobs. MBAs are especially popular since the degree is usually meant to prepare someone for more advanced, leadership roles in business (or even government). But is an MBA degree worth the extra years of schooling -- especially when you could be spending that time working full-time?
At first glance, the numbers indicate that the answer is a definite yes. A recent survey of accounting/financial workers of varying skill and seniority levels found that CFOs without a degree had an average salary of only $38,920, those with a Bachelors Degree earned $88,836, and MBAs earned an average of $104,284. The return on investment for an MBA certainly seems worthwhile. Some studies indicate the MBAs earn up to 145% more over their lifetime than non-degree holders. So getting your MBA, while sometimes expensive, is certaining economical.
However, there are many mitigating factors affecting an online MBA. Keep in mind that the salary figures quoted above are fairly flexible and can vary widely based on a number of factors. For instance, the type of work you're going into can make a huge difference; consulting jobs will often pay more than finance/accounting jobs, though each could have a different compensation/bonus structure. Your previous experience also speaks volumes. If you're fresh out of business school and go hunting for an investment banking job after years in a marketing firm, odds are good that your starting salary will be much lower than someone with greater comparable experience.
An online MBA is still a very good idea. The numbers are still very persuasive. Statistics from the Graduate Management Admissions Council (the folks who administer the GMAT) indicate that in many cases someone's pre- and post-MBA salary can jump 50% or more. For example, someone working in marketing making an average of $42,000 before getting their MBA can make an average of $80,000 after receiving their degree. That's nearly doubling your money!
An MBA may not be equivalent to a winning lottery ticket, but the odds are good that your earnings will increase after earning your degree -- making those extra years of school worthwhile. Just be sure that you're pursuing the right degree for the right reasons and, of course, good luck with that graduate school application!
Access eLite's
Degree,
MBA,
MBA Degree Online,
Online MBA,
Online MBA Degree Programs
What is SSH (Secure Shell)?
What is SSH (Secure Shell)?
SSH (Secure Shell) is a protocol for creating a secure connection between two computers.
SCP and SFTP - Secure File Transfer Using SSH
SCP and SFTP are replacements for the legacy `cp` and `ftp` file transfer applications.
SCP and SFTP enable secure encrypted file transfer over an SSH connection.
Free SSH Servers . . .
There are several free SSH implementations available. Some support only SSH, while others also support SCP and SFTP.
[Operating Systems Supported: AIX, HP-UX, Irix, Linux, NeXT, SCO, SNI/Reliant Unix, Solaris, Digital Unix/Tru64/OSF, Mac OS X, and Cygwin]
[Operating Systems Supported: Linux, Mac OS X, FreeBSD, NetBSD, OpenBSD, Solaris, Irix, True64, AIX, HP-UX]
Free SSH Clients . . .
[Operating Systems Supported: AIX, HP-UX, Irix, Linux, NeXT, SCO, SNI/Reliant Unix, Solaris, Digital Unix/Tru64/OSF, Mac OS X, and Cygwin]
[Operating Systems Supported: NetBSD, FreeBSD, Linux]
[Operating Systems Supported: GNU/Linux on Sparc, Intel, PPC and Alpha, FreeBSD, Solaris and IRIX]
[Operating Systems Supported: Windows]
[Operating Systems Supported: Win32 and Unix]
[Operating Systems Supported: Windows]
[Operating Systems Supported: Windows (SCP and SFTP, no SSH)]
[Operating Systems Supported: Macintosh]
[Operating Systems Supported: Macintosh]
[Operating Systems Supported: Macintosh (SFTP only)]
[Operating Systems Supported: Palm OS]
[Operating Systems Supported: Palm OS]
Access eLite's
Dropbear SSH Server,
free,
free ssh servers,
FreeSSH,
lsh,
open,
OpenSSH,
scp,
secure shell,
server,
sftp,
SSH,
SSHD-NT
Bypassing Websense using HTTP Tunneling
Bypassing Websense using HTTP Tunneling
You can also bypass Websense by using HTTP Tunneling. HTTP Tunneling programs work well to bypass Websense. Most programs also come with options, which help you to destroy the history of your Internet and Widows activity. What this means is that you can ensure comfort and security of your online activities and can spoof your web browser information, which helps to thwart hacking missions. One can download HTTP Tunneling software programs from the Internet quite easily and inexpensively.
Access eLite's
bypass,
bypassing,
Bypassing Websense using HTTP Tunneling,
http,
HTTP Tunnel,
tunnel,
websense
Configure a Web Proxy in Mozilla Firefox
Configure a Web Proxy in Mozilla Firefox
- Note the IP address and the port number of that proxy server.
- Open Firefox.
- Open the Tools menu.
- Select Options.
- Click the Connection Settings button.
- Check Manual Proxy Configuration.
- Enter the IP address of the proxy you selected into the "HTTP Proxy:" box.
- Enter the port number of the proxy you selected into the corresponding "Port:" box.
- Enter the IP address of the proxy you selected into the "SSL Proxy:" box.
- Enter the port number of the proxy you selected into the corresponding "Port:" box.
- Click the OK button.
- Click the OK button.
Access eLite's
Configure a Web Proxy in Mozilla Firefox,
Dropbear SSH Server,
firefox,
http,
proxy,
ssl,
ssl proxy
Configure a Web Proxy in Internet Explorer
Configure a Web Proxy in Internet Explorer
- Note the IP address and the port number of that proxy server.
- Open Internet Explorer.
- Open the Tools menu.
- Select Internet Options.
- Click on the Connections tab.
- Click on the LAN Settings button.
- Check the box next to "Use a proxy server for your LAN".
- Enter the IP address of the proxy you selected into the "Address:" box.
- Enter the port number of the proxy you selected into the "Port:" box.
- Click the OK button.
- Click the OK button.
Access eLite's
Configure a Web Proxy in Internet Explorer,
Explorer,
Internet,
Internet Options,
lan
How to find Hostname
How to find Hostname
There are different kinds of hosts like your local computer, ISP, web server etc. Here I’m going to tell you how to find hostname.
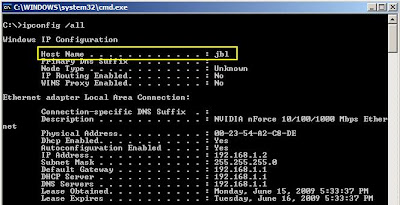
Local Hostname – To find localhost name, just open Command Prompt [CMD] and type “hostname” to get the local hostname on you computer. Also, you will get the hostname by typing “ipconfig /all”.
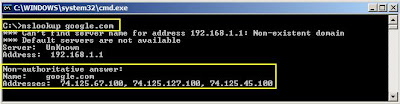
IP or Domain Hostname – You can also fine IP/ Domain hostname from DOS. Just type “nslookup domain.com” to get host IP address. For example if we type “nslookup google.com” then the output will be as follows . . .
Similarly, you can find the domain hostname by typing “nslookup xxx.xxx.xxx.xxx”
For example, if you type Google’s IP 74.125.67.100 then it will give you the output as below:
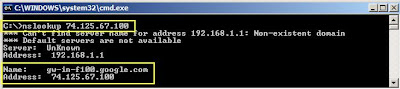
Now, if you try this command with your domain, it will give you the IP address. Next, you may get error [see the screenshot below] while trying to get the domain from IP lookup. It’s because your domain is on a shared IP. :) It’s only possible if your domain is on a dedicated IP Address.
How to find Subnet Mask
How to find Subnet Mask
If you want to find your subnet mask of the network or if you are in the network but want to know what is my subnet mask, here is a handy article for you. Subnet mask helps to identify which section of an IP address is reserved for network and which part is available for the use of host. Subnet mask is also known as netmask. Now I’m going to tell you how to find subnet mask on your local network.
Windows Vista/ XP/NT/2003 – On Windows Vista, XP or other NT versions you can follow simple steps below.
[1] Go to Start Menu -> Run
[2] Type “cmd” and press enter to open the command prompt window.
[3] Now type “ipconfig /all” [without quotes]
You will get the subnet mask on your local network like the following screenshot.

Also you get the same information from the properties of Local Area Network. Just go to Start Menu -> Settings -> Network Connections and double click the Local Area Network icon. Then just click on the support tab at the top of the window.

Linux/ Unix – On Linux or Unix system just type following commands on shell to get the subnet mask.
$ ifconfig
or
$ /sbin/ifconfig
or
$ /sbin/ifconfig interface-name
The output will be as follows…
lnc0: flags=108843 mtu 1500
inet 72.122.61.51 netmask 0xfffffff8 broadcast 72.122.61.55
ether 00:0c:29:32:8a:8c
plip0: flags=108810 mtu 1500
lo0: flags=8049 mtu 16384
inet6 fe80::1%lo0 prefixlen 64 scopeid 0×3
inet6 ::1 prefixlen 128
inet 127.0.0.1 netmask 0xff000000
The netmask is the subnet mask and displayed in hexadecimal format.
Open Proxy Closed Proxy
Open Proxy Closed Proxy
Open proxy
Open proxy
An open proxy is a proxy server that is accessible by any Internet user. Generally, a proxy server allows users within a network group to store and forward Internet services such as DNS or web pages to reduce and control the bandwidth used by the group. With an open proxy, however, any user on the Internet is able to use this forwarding service.
Advantages
So-called "anonymous" open proxies allow a user to conceal his or her IP address from the accessed service, as it is possible to use someone else's computer in order to hide one's identity and/or location. This is sometimes used to abuse or interrupt the accessed service, potentially violating its terms of service or some laws; open proxies are therefore often seen as a problem. However, anonymous open proxies increase the user's anonymity or security when browsing the web or using other Internet services: a user's true IP address can be used to help deduce information about that user as part of an attempted computer crack. Furthermore, open proxies can be used to circumvent efforts at Internet censorship by governments or organizations. Several web sites provide constantly updated lists of open proxies.
Disadvantages
It is possible for a computer to run as an open proxy server without the computer's owner knowing this. This can result from misconfiguration of proxy software running on the computer, or from infection with malware (viruses, trojans or worms) designed for this purpose. If it is caused by malware, the infected computer is known as a zombie computer. There are hundreds of thousands of open proxies online. This is rarely a matter of misconfiguration, in most cases an open proxy is unknown to the server owner. Using an open proxy can be legally dangerous: the current law in Germany, for example, makes it illegal to access a computer or network without the owner's knowledge, even if the proxy is not password-protected. There are no reasons to run a clean open proxy for an organisation, so any open proxy is suspicious. The main sign of a legal open proxy is the fact that it is not anonymizing the connection.
Running an open proxy is a high risk for the server operator; providing an anonymous proxy server can cause real legal troubles to the owner. Such services are frequently used to break into foreign computer systems, child pornography is usually consumed through proxies, and illegal content is likely to be spread through such proxies. Also, such a proxy can cause a high bandwidth usage resulting in higher latency to the subnetwork and violation of bandwidth limits. A wrongly configured open proxy can also allow access to a private subnetwork or DMZ: this is a high security concern for any company or home network because computers that usually are out of risk or firewalled can be directly attacked.
Many open proxies run very slowly, sometimes below 14.4 kbit/s, or even below 300 bit/s, while other times the speed may change from fast to slow every minute. Some, such as PlanetLab proxies, run faster and were intentionally set up for public use.
Because open proxies are often implicated in abuse, a number of methods have been developed to detect them and to refuse service to them. IRC networks with strict usage policies automatically test client systems for known types of open proxies. Likewise, a mail server may be configured to automatically test mail senders for open proxies, using software such as proxycheck. Increasingly, mail servers are configured out of the box to consult various DNSBL servers in order to block spam; some of those DNSBLs also list open proxies.
Closed proxy
A closed proxy is a proxy server that is only accessible to specific individuals because it only allows users within its area connect to it and/or requires a username and password.
Access eLite's
anonymous,
Closed proxy,
Configure a Web Proxy,
DNS,
Explorer,
Internet Explorer,
isp,
Open proxy,
proxy
Proxy
Proxy
Proxy may refer to one who or that which acts on behalf of someone or something else, as in:
> Proxy bomb, a bomb delivered by a person against their will
> Proxy card, a substitute card used in trading card games when a player does not own the substituted card and also can occur when proxy cards are not tradable
> Proxy fight, attempting to influence how company shareholders use their proxy votes
> Proxy marriage, common amongst European monarchs, where one party is not present in person to their marriage to the other
> Proxy murder, a murder which the murderer commits at the behest of another
> Proxy voting, a vote cast on behalf of an absent person
> Proxy war, a war where two powers use third parties as a substitute for fighting each other directly
Technical Terms:
> Proxy (statistics), a measured variable used to infer the value of a variable of interest
> Proxy (climate), a measured variable used to infer the value of a variable of interest in climate research
> Proxy authentication connects one user through another, generally to authenticate through multiple tiers in a computer system.
> Proxy pattern, a software design pattern in computer programming
> Proxy server, a computer network service that allows clients to make indirect network connections to other network services
Pay per click
Pay per click (PPC)
Websites that utilize PPC ads will display an advertisement when a keyword query matches an advertiser's keyword list, or when a content site displays relevant content. Such advertisements are called sponsored links or sponsored ads, and appear adjacent to or above organic result on search engine results pages, or anywhere a web developer chooses on a content site.
Although many PPC providers exist, Google Adwords, Yahoo! Search Marketing, and Microsoft adCenter are the three largest network operators, and all three operate under a bid-based model. Cost per click (CPC) varies depending on the search engine and the level of competition for a particular keyword.
Pay per click (PPC) is an Internet advertising model used on search engines, advertising networks, and content sites, such as blogs, in which advertisers pay their host only when their ad is clicked. With search engines, advertisers typically bid on keyword phrases relevant to their target market. Content sites commonly charge a fixed price per click rather than use a bidding system.
Websites that utilize PPC ads will display an advertisement when a keyword query matches an advertiser's keyword list, or when a content site displays relevant content. Such advertisements are called sponsored links or sponsored ads, and appear adjacent to or above organic result on search engine results pages, or anywhere a web developer chooses on a content site.
Although many PPC providers exist, Google Adwords, Yahoo! Search Marketing, and Microsoft adCenter are the three largest network operators, and all three operate under a bid-based model. Cost per click (CPC) varies depending on the search engine and the level of competition for a particular keyword.
The PPC advertising model is open to abuse through click fraud, although Google and other search engines have implemented automated systems to guard against abusive clicks by competitors or corrupt web developers.
Access eLite's
addwords,
AdWords,
AdWords campaign,
click fraud,
cpc,
fraud,
Pay per click,
ppc
How to block people on Facebook
How to block people on Facebook
Facebook now is loaded with spammers, online marketers and nasty people who often disturb others by sending unwanted messages and leaves you no option but to block them. If you don’t know how to block people on facebook, its pretty simple.
You can Block people (friends) on Facebook with simple steps as mentioned below:

[1] First log in to your Facebook account the on the homepage click on the “setting” link at the top bar and select Privacy Settings.
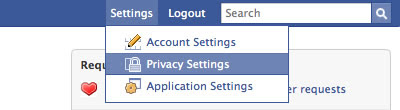
[2] Now you can simply search the person you want to block.
[3] Next, you will get an option next to their name. Just choose Block and you are done.
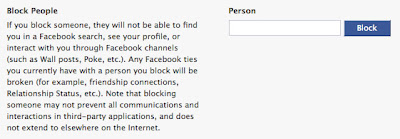
On the other hand you can also set up a Limited Profile on Facebook to get rid of unwanted people. Just follow the steps below …
[1] Log in to your Facebook account.
[2] Now, go to the My Privacy page.
[3] Next click on the Limited Profile Settings link. Face will give you a snapshot of your limited profile with a list shared features.
[4] Just select the features you want to share with your limited profile and click SAVE when you are done.
[5] Now you can add friends to this profile and only confirmed friends are allowed.
Access eLite's
block people,
block people on Facebook,
facebook,
Privacy
Difference between CDMA and WCDMA
Difference between CDMA and WCDMA
I just covered difference between CDMA and GSM, here is another article on similar technology WCDMA. lLet’s see what is the difference between CDMA and WCDMA
WCDMA comes from Wideband Code Division Multiple Access and CDMA, as you may guess, comes from Code Division Multiple Access. Apart from their almost the same name the two technologies don’t share much characteristics.
WCDMA is a system developed by NTT DoCoMo from Japan, based on CDMA2000 but very different. While CDMA2000 works with several pairs of 1.25 MHz frequency, the WCDMA uses a pair of 5 MHz. It may look like its big fat brother but it’s not.
Economically speaking, CDMA and WCDMA are rivals, with the balance leaning towards CDMA due to its better performance – cost ratio. WCDMA, as well as CDMA, are the basis for 3rd generation (3G) communication standard. But WCDMA goes with 3G UMTS, GSM’s best friend, with increased coverage ad low costs. 3G UTMS give you high data transmission on the internet, video calls and a lot more mobile services. It also gives you the possibility to send multiple data simultaneously, you can talk to the phone, send a text message (SMS) and check your email in the same time from your phone.
If you don’t have 3G coverage all over but you still want / need to keep it activated don’t worry, the cell phones are build to switch automatically to GSM mode when thet lost the 3G connection.
Know WhoIS info of site with DOS prompt
Know WhoIS info of site with DOS prompt
Here I’m going to tell you one very interesting way to get WhoIS information of any domain or IP address from your desktop. Yes, mostly or say almost all time we need to depend on different WhoIS websites. But, you can easily get all WhoIS information directly from DOS Command Prompt just by typing “whois www.domain.com” [without quote]. You will get the output on your DOS screen like this…

In Linux Shell you can direct get WhoIS information, but to obtain it from DOS you need to install a small EXE from Microsoft’s TechNet Webstie. You can download this EXE from here. After downloading, extract the EXE file to your System folder. [e.g. \Windows \ System32 or WinNT \ System32. If you are using Windows98 then \Windows\ System ]. That’s all, now simply type whois followed by any domain name or IP address on your command prompt and get all details. But, obviously this command will only work when you are connected with Internet.
Access eLite's
dos,
IP address,
linux,
WhoIS
How to increase speed of Internet
A faster Internet connection is everybody’s dream even though you may have the fastest Internet connection in the world. That is how we feel when it comes to the information that comes through the Internet.
Following are a few tips and tricks that will help to make your existing Internet connection faster. Please remember, faster Internet does not necessarily mean more bandwidth!
Windows XP Tweak
1. Login to your computer as an Administrator.
2. Click ‘Start’ and then click ‘Run’.
3. Type ‘gpedit.msc’ and press enter.
4. Click ‘+’ sign of ‘Local Computer Policy’.
5. Click ‘+’ sign of ‘Administrative Templates’.
6. Click ‘+’ sign of ‘Network’.
7. Highlight ‘QoS Packet Scheduler’.
8. Click ‘Limit Reservable Bandwidth’ and make is enabled.
9. Now set the value of ‘Bandwidth limit %’ to ‘0’ (zero).
10. Close the window.
[This will enhance the speed of the Internet connection once you restart the computer.]
Change your router
If you use a wireless router to connect to the Internet and it is slow, changing the router may help. There can be many reasons behind slow wireless Internet connections and the following are common issues.
• Low signal strength
When the wireless signal strength is low, you usually get a lower surfing speed. Changing the location of the wireless router or buying a new router with high signal capability will enhance the surfing speed.
• Low bandwidth router
‘g’ and ‘b’ classes are the most common for current wireless routers. If your Wi-Fi network is used by many users, high bandwidth ‘n’ class routers will definitely help.
• Router has not been configured properly
Many home-used wireless routers are used with factory settings. These settings may not be ideal for your broadband connection. Read the manual or get professional help to tweak and speedup the Internet connection.
Disable heavy web content
Heavy web content such as images and flash animations consume more bandwidth than you ever imagine. If you use a dial-up connection, these will turn out to be disasters. Web browser plug-ins (Ex: Flashblock Firefox extension) are used for blocking download of flash content, so the user experiences faster Internet.


